**TL;DR**
Vendor relationships rarely break all at once. They fail quietly. A missing control here. A vague answer there. An assumption that someone else is handling compliance. By the time a real issue appears, the vendor is deeply embedded in workflows, dashboards, or products. Unwinding that relationship becomes painful.
What is a Vendor Audit Checklist?
That is why a vendor compliance checklist matters. Not as a procurement formality, but as a working tool for data, risk, and governance teams. A good checklist forces clarity. It makes expectations explicit. It surfaces weak signals before they turn into operational or legal problems.
Most organizations do some form of vendor review. Few do it well. The common mistake is focusing only on contracts, certifications, or high-level assurances. Those documents describe intent. They rarely describe how data is actually collected, processed, stored, or reused. A meaningful data audit goes deeper. It asks how controls are enforced in practice. It looks at technical safeguards, operational discipline, and evidence. It examines how vendors respond when conditions change, not just when everything is stable.
This article is written for teams that want to build a vendor audit checklist that actually works. We will walk through what a strong checklist covers, how to structure it for repeat use, and where organizations usually underestimate risk. The goal is not to create paperwork. It is to reduce uncertainty before it becomes costly.
Why Vendor Audits Fail Without a Structured Checklist
Most vendor audits fail for a simple reason. They rely on conversation instead of structure. Meetings happen. Questions are asked. Notes are taken. Everyone feels reasonably confident. And yet, months later, gaps appear that no one remembers approving. A vendor compliance checklist exists to prevent that drift.
Audits become subjective too quickly
Without a checklist, audits depend heavily on who is in the room. One reviewer focuses on contracts. Another focuses on certifications. A third assumes technical safeguards exist because the vendor “sounds mature.”
None of this is malicious. It is human. A structured checklist removes interpretation from the equation. The same questions are asked every time. The same evidence is expected. Answers are recorded in a way that can be revisited later. This is what turns an audit into a process instead of a discussion.
Risk hides in the gaps between teams
Vendor audits often span multiple functions. Legal looks at terms. Security looks at controls. Data teams look at outputs. Procurement looks at cost. Without a shared checklist, each team sees only part of the picture. The result is false confidence. No single team sees a red flag, but the combination of small gaps creates real exposure. A vendor compliance checklist forces those gaps into the open by aligning everyone around the same review framework.
Assurances replace evidence
Another common failure is accepting assurances instead of proof.
Vendors say they are compliant. They say data is handled securely. They say controls are in place. A checklist shifts the focus from claims to evidence. What logs exist. What controls are automated. What happens when something breaks. How incidents are detected and handled. This is especially important for data vendors, where issues often surface long after onboarding.
If you are evaluating vendors involved in consent-aware or automated data collection, this overview of user consent scraping and compliance automation highlights the kind of operational detail that audits often miss.
One-time reviews create long-term risk
Many organizations treat vendor audits as one-time events. The checklist gets filled. The vendor is approved. The document is filed away. Real risk appears later, when vendors expand scope, change infrastructure, or introduce new data sources
Why structure changes outcomes
Structure does not slow audits down. It speeds them up. When expectations are clear, vendors respond faster. When questions are consistent, answers are easier to compare. When evidence is required, weak controls surface early.That is the real value of a vendor compliance checklist. It replaces assumptions with visibility.
If you're evaluating whether to continue scaling DIY infrastructure or move to govern global feeds, this is the conversation to have.
What a Strong Vendor Compliance Checklist Must Cover
A useful vendor compliance checklist does not try to cover everything. It covers the things that actually fail in real vendor relationships. The goal is not completeness. It is risk visibility.
Data handling comes first
If a vendor touches your data, data handling deserves the most attention.
A checklist should clearly ask:
- What data is collected and from where
- Whether personal or sensitive data can appear, intentionally or accidentally
- How data is filtered, masked, or anonymized
- Where data is stored and for how long
This is where many audits stay vague. “We handle data securely” is not an answer. A checklist should require specifics, ideally backed by examples or documentation.
For vendors involved in automated collection or enrichment, it helps to align these questions with privacy-safe practices. This overview of privacy-safe scraping and PII masking explains the kinds of controls that should show up during audits.
Governance and accountability need to be explicit
Good vendors can explain who is responsible when something goes wrong.
A checklist should ask:
- Who owns data governance internally
- How decisions around access, reuse, and deletion are made
- What escalation paths exist for incidents or disputes
- How changes to scope or data sources are approved
If responsibility is vague, accountability usually is too.
Evidence matters more than promises
One of the simplest ways to strengthen a checklist is to ask for evidence. Logs. Sample reports. Incident response summaries. Audit artifacts. Even anonymized examples help. Vendors that operate mature systems usually have this material ready. Vendors that rely on manual processes often struggle. That difference is a valuable signal.
The checklist should be usable, not theoretical
Finally, a checklist should be practical. Questions should be clear enough that different reviewers interpret them the same way. Answers should be comparable across vendors. Follow-up actions should be obvious. If a checklist cannot be reused across vendors and over time, it will slowly be ignored.
Designing the Checklist: Categories and Structure That Work
Once you know what needs to be covered, the next challenge is structure. This is where many teams overcomplicate things. They create long documents filled with overlapping questions, legal language, and vague scoring. The result looks thorough but is hard to use. A good vendor compliance checklist is structured to be answered, reviewed, and revisited.
Start with clear sections, not random questions
The checklist should be grouped into a small number of logical categories. This helps reviewers focus and helps vendors understand what is being evaluated. A practical structure usually includes:
- Data collection and handling
- Privacy and compliance controls
- Security and infrastructure
- Governance and accountability
- Operational resilience
- Auditability and evidence
Each section should answer a simple question. Can this vendor be trusted with this aspect of our operations? If a section does not map to a clear risk area, it probably does not belong.
Keep questions specific and testable
Checklist questions should be written so they can be answered clearly.
Avoid questions that invite marketing language. “Do you follow best practices?” rarely produces useful information. Instead, ask questions that force detail. How is access controlled? Where are logs stored? How long is data retained. What happens when a policy changes. Specific questions reduce ambiguity and make follow-up easier.
Design for comparison, not perfection
One of the most useful outcomes of a vendor compliance checklist is comparison. You want to see where vendors differ, not just whether they pass. That means questions should be consistent across vendors and phrased in a way that makes differences obvious. This discussion on staying ahead with real-time data shows why operational discipline matters as much as feature sets.
Leave room for evidence and notes
A checklist should not just collect answers. It should collect context. Each section should allow reviewers to note evidence, concerns, and follow-up actions. This is what turns a checklist into a working audit record instead of a static form. Over time, these notes become valuable history. They show how vendors evolve and where risk has increased or decreased.
Make it reusable by default
The best checklists are reused. They are updated as regulations change. They are applied when scope expands. They are referenced when incidents occur. Designing for reuse means keeping language clear, avoiding one-off assumptions, and treating the checklist as part of governance, not procurement paperwork.
Running the Audit: How to Use the Checklist Effectively
A vendor compliance checklist only creates value if it is used well. Many teams build solid checklists and then weaken them during execution. Questions are skipped to save time. Evidence is promised later. Follow-ups are left open-ended. Over time, the checklist becomes ceremonial. Running the audit properly requires discipline, not aggression.
Treat the checklist as a working document
Each question should be answered in writing. Verbal assurances should be captured and validated later. If an answer is unclear, that uncertainty should be recorded, not smoothed over. This creates a shared reference point. Weeks or months later, there is no debate about what was said or assumed.
Ask for evidence at the right moments
If a vendor claims automated controls, ask for logs or architecture diagrams. If they claim compliance processes, ask for examples of how changes are handled. If they claim strong governance, ask who signs off on exceptions. The goal is not to overwhelm vendors. It is to see whether controls exist beyond policy language.
Use the audit to surface trade-offs
Not every gap is a deal-breaker. A good audit makes trade-offs explicit. A vendor might be strong on security but weaker on auditability. Another might be transparent but less automated. The checklist helps teams decide consciously instead of discovering trade-offs accidentally later.
Document outcomes and next steps
Every audit should end with clear outcomes. What risks were accepted. What gaps need remediation. What follow-ups are required. What timeline applies. Without this step, audits feel complete but change nothing.
Example: Vendor audit checklist in action
| Checklist area | Question asked | Vendor response | Evidence reviewed | Risk level | Follow-up action |
| Data handling | Can personal data appear in collected datasets | Yes, in edge cases | Sample dataset with masked fields | Medium | Confirm masking happens at ingestion |
| Privacy controls | How is PII masked or anonymized | Automated masking rules | Pipeline diagram and logs | Low | None |
| Governance | Who approves data reuse | Data governance committee | Internal policy document | Medium | Request escalation workflow |
| Security | How is access controlled | Role-based access | Access control list | Low | None |
| Auditability | Can you show lineage for a dataset | Partial lineage available | Sample lineage report | Medium | Request full lineage coverage |
| Operations | How are incidents handled | Manual escalation | Incident summary | Medium | Review response SLAs |
This kind of table keeps the audit grounded. It shows where risk exists and what is being done about it.

Figure 1: The four verification areas that determine whether a vendor audit produces real risk visibility.
Why this approach holds up over time
Audits run this way and scale better. They are easier to repeat. Easier to compare. Easier to defend. When vendors change, the checklist adapts. When questions arise later, decisions are documented. That is the real payoff of a vendor compliance checklist. Not compliance theater, but durable risk management.
Where Vendor Audits Commonly Miss Risk
Even teams with solid checklists tend to miss the same kinds of risk. Not because the questions are wrong, but because attention drifts to what is easy to verify instead of what actually breaks. This section is about those blind spots.
Over-indexing on certifications
Certifications feel reassuring. ISO. SOC. Compliance badges. They matter, but they are not a substitute for understanding how a vendor actually operates day to day. Certifications describe controls at a point in time. They do not explain how those controls behave under pressure, change, or scale. A vendor can be certified and still struggle with data drift, delayed deletions, or undocumented reuse. Audits that stop at certificates miss operational reality.
Treating data outputs as the only risk surface
Many audits focus heavily on what data the vendor delivers. Much less attention is paid to how that data is produced. Where does it originate? What happens before transformation. What temporary storage exists. What logs are retained. Who can see raw inputs? This is especially risky for data vendors, where upstream collection methods and intermediate systems often carry more exposure than the final dataset. A proper data audit looks upstream, not just at what lands in your warehouse.
Ignoring change management
Vendors evolve. They add sources. They change infrastructure. They refactor pipelines. They onboard new teams. Each change can quietly alter risk. Audits often capture a snapshot and then assume stability. That assumption is rarely correct. Strong checklists ask how changes are reviewed, communicated, and approved. Weak ones assume today’s answers will still be true next quarter.
Assuming internal use means low risk
Another common miss is internal reuse. Teams assume that if data stays internal, risk is limited. In practice, internal reuse is where scope creep happens fastest. New teams access old datasets. New use cases emerge. Old assumptions are forgotten. Vendor audits should ask how internal access is controlled and how reuse decisions are governed, not just whether data is shared externally.
Underestimating exit and offboarding risk
Most audits focus on onboarding. Very few focus on exit. What happens to data when a vendor relationship ends. How quickly can access be revoked? How is deletion verified? What evidence is provided. Offboarding is where weak governance shows up clearly. If a vendor cannot explain this cleanly, risk remains even after the contract ends.
Why these misses repeat
These gaps persist because they are uncomfortable. They require deeper questions. They slow down decisions. They surface trade-offs teams would rather avoid. But these are exactly the areas where real risk lives. A vendor compliance checklist that does not address them creates confidence without control.
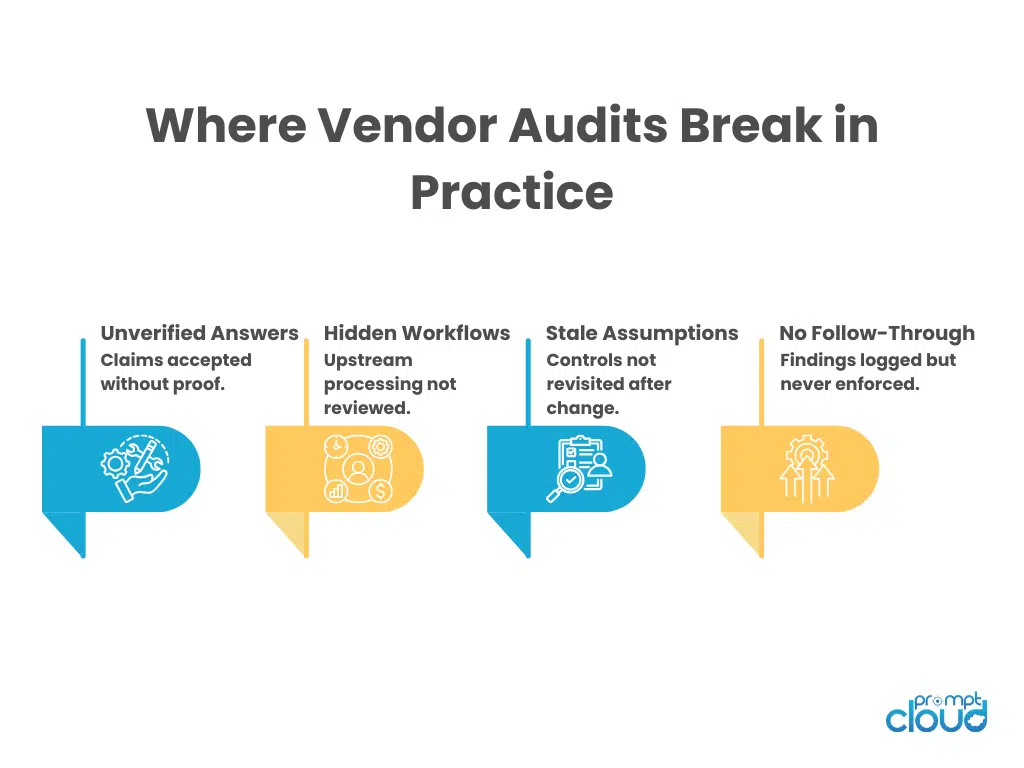
Figure 2: The most common failure points that cause vendor audits to miss real, operational risk.
Closing the Loop: Turning Audit Findings Into Ongoing Governance
An audit is only useful if it changes what happens next. Most teams do the hard part, they run the vendor review, capture answers, identify gaps, and then stop. The checklist gets filed. The vendor gets onboarded. And the same risks quietly return six months later in a new form. Ongoing governance is how you prevent that loop.
Convert findings into three buckets
After the audit, every finding should land in one of these buckets:
- Acceptable risk
You understand the gap, you accept it knowingly, and you document why. - Fix required before go-live
Controls are missing or unclear enough that onboarding should pause. - Fix required with a deadline
The vendor can proceed, but must deliver changes by a specific date, with evidence.
This sounds basic, but it is the difference between a data audit that changes behavior and one that becomes a record of missed opportunities.
Make the checklist part of vendor operations
A vendor compliance checklist should not live only in procurement. It should show up:
- during quarterly business reviews
- when data scope expands
- when new sources or regions are added
- after incidents or outages
- before renewals
This turns the checklist into a system of record. It also makes follow-ups easier, because you are not restarting from scratch every time.
Track risk like you track performance
If you measure vendors only on delivery, you incentivize speed over control. The better pattern is to track risk indicators alongside performance indicators. Things like:
- frequency of scope changes
- evidence completeness
- response time to audit questions
- deletion and retention adherence
- incident transparency
If your vendor relationship depends on time-sensitive data, governance should also cover timeliness, change detection, and reliability, because these factors often drive risky shortcuts. A practical example is how teams structure monitoring programs in a price monitoring strategy, where stability and consistency matter as much as coverage.
Close with evidence, not confirmations
Every remediation item should end with evidence. If the vendor claims a control is implemented, the checklist should require proof. Logs, screenshots, test results, audit artifacts, updated diagrams. Anything that makes the control verifiable. This keeps governance from becoming a cycle of promises.
The real goal
The goal is not to “pass an audit.” The goal is to reduce surprises. A vendor audit checklist works when it makes risk visible early, forces decisions to be explicit, and creates a trail that future teams can follow without guessing what happened. That is what turns a one-time review into governance that holds up.
For a neutral, authoritative framework on third-party and supply-chain risk management, refer to: NIST guidance on supply chain risk management.
If you're evaluating whether to continue scaling DIY infrastructure or move to govern global feeds, this is the conversation to have.
FAQs
What is a vendor compliance checklist?
A vendor compliance checklist is a structured set of questions used to evaluate how third parties handle data, manage risk, and enforce governance controls. It replaces informal reviews with repeatable audits.
How is a data audit different from a security audit?
A data audit focuses on how data is collected, processed, stored, reused, and deleted. A security audit focuses on infrastructure protection. Both matter, but they answer different risk questions.
How often should vendor audits be performed?
At minimum during onboarding and renewal. Mature teams also revisit audits when scope changes, new data sources are added, or incidents occur.
Should vendors be disqualified for every audit gap?
Not necessarily. The goal is to surface and classify risk. Some gaps are acceptable if documented and time-bound remediation plans exist.
What evidence should vendors provide during an audit?
Examples include logs, architecture diagrams, data flow explanations, incident summaries, lineage records, and retention or deletion proofs.