Data thefts have existed ever since organizations started collecting and storing data but it wasn’t as easy when it was mainly stored in paper records or files. The electronic formats of data storage make it accessible from remote locations and can be transmitted easily. Therefore, Data privacy is a crucial factor in today’s world. With advancement in technology, hacking and crawling of data are creating new level of threats. Maintaining Data Security and Privacy is a relentless process and requires regular monitoring of online activities. Securing data involves preventing data from unauthorized access, infection, malware attack, corruption and others as well.
Leveraging the multiple cloud services, users are now storing their files on cloud to save space in their devices. Now the question arises, “How safe is your data on the cloud?” Cloud services have several disadvantages especially the ones that are free and are still making profit. The first and foremost concern of using cloud services is privacy. Companies are mining data stored in cloud for advertising and marketing purposes. This data could even be hacked or stolen. Your personal data can be sold or published without your consent or worse.
There are concerns associated with cloud providers as these can suspend or cancel your account leading to loss of your data. However, large enterprises have better-designed and well-executed security policies but still have concerns over fresh data that keeps coming up. Professionals need to be cautious while using email for business as they are dealing with their own data as well as that of their organization. People may also be concerned about keeping data private within a private network to ensure protection of their information.
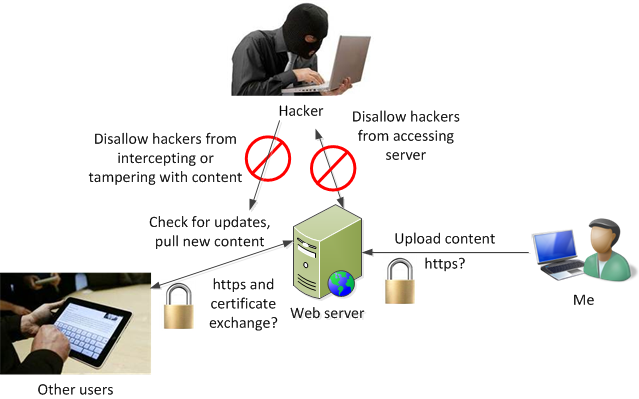
Secure Data Transmission is a critical issue as hackers may alter the information while it is on its way to reach the intended recipient. However, instead of reaching the intended recipient the message is transmitted over faulty channel leading to serious online offenses. Almost all types of Data Transmissions can be intercepted by hackers and cyber criminals. Therefore, one needs to be extremely cautious while transmitting secure information. There is growing risk of data interception from the communication channel through electronic eavesdropping or by stealing recipient password. Transmission occurs either through air or wire and generally it is more secure when transmitted through wire than air as it required the hacker to be physically present near the wire for interception. However, interception during air transmission can occur from anywhere within reach of the signal.
Packet Sniffing and IP Spoofing are the common thefts to hack private information over a network. Packet sniffing enables in capturing data while it is being transmitted over a network. Spoofing is a technique to gain unauthorized access to a computer with an IP address showing message is from a trusted host. Regardless of how it happens, data thefts must be prevented by using secure channels to transfer data.
If the data seems to be in a compromised state, then Secure Data Recovery is the only way to retrieve information from damaged, corrupted, failed or hard to access storage media. The data usually needs to be retrieved from CDs, DVDs, hard disk drives and other hardware. Recovery is possible only in the case of physical or logical damage to the file system. We can’t recover the data if it is stolen.
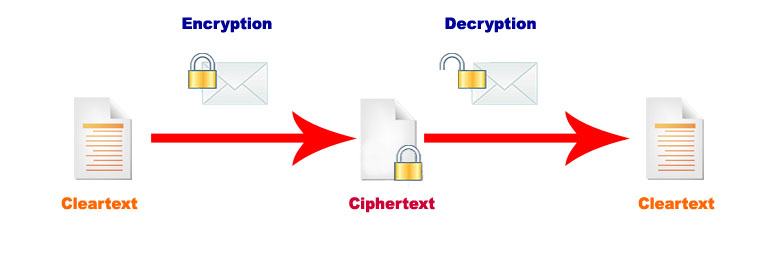
Data Security Management maintains data integrity along with preventing data from unauthorized access. It is extremely essential for safeguarding critical data and ensuring data protection. Several encryption techniques are available to ensure safety of information over a communication channel. Encryption involves translating plain text into cipher text using encryption key. This Cipher text is converted into plain text at receiver’s end using decryption key. Encryption allows any message to be transmitted without the fear of interception. Encryption is of two types:
- Private Key Encryption
- Public Key Encryption
Private Key Encryption
In Private Key Encryption or Symmetric encryption, each party must possess knowledge of how to interpret the message before the message is sent. It is especially used for high level of data security and privacy. For instance, army men have a code language which they follow to authenticate each other’s identity.
Public Key Encryption
There are several public key encryption methods to ensure privacy. PGP (pretty good privacy) is one of the most common amongst them. In this method, you can exchange messages with people possessing a unique identification key. After receiving a key from someone, your PGP software will be using the key to encode a message that only you can interpret. This PGP method enables you to encode a message that will be decrypted using your public key.
Information security involves preventing unauthorized access, malware or virus attack, infection or corruption of information. Encryption is one of the most common ways to provide tiered data-security. To ensure maximum information security, companies must understand applicable threats, align appropriate layers of security, and ensure continuous monitoring of activities. Logical security can be offered using firewalls, running antispyware, and anti-virus on servers and other storage systems. Physical security can be offered using access controls, changing key-code regularly and informing only those who require access.
Today, many companies are offering comprehensive data security solutions to prevent data loss, prior indication of threats, and optimum data protection. This data could include personal records, organization’s intellectual property, and at times, something very confidential. Irrespective of the evolution in data collection, storage, and sharing technology, there will be a never-ceasing need to take stock of the safety and security of data that we gather, store, and disseminate.