A few years ago, a mid-sized logistics company noticed something odd. Their network traffic looked normal. No alarms were going off. Yet, something did not feel right. Their IT team pulled intelligence reports from their threat data sources, and there it was. A pattern of probing behavior, subtle enough to dodge traditional defenses but obvious to anyone looking at the broader intelligence picture.
Because they had the right threat intelligence in place, they caught a credential harvesting operation before it turned into a full-scale ransomware attack. They saved millions of dollars in potential damages and, more importantly, kept their customers’ trust.
This is what cyber threat intelligence does. It is not about reacting to disasters. It is about seeing the storm before the first clouds even appear.
What Is Threat Intelligence, Really?
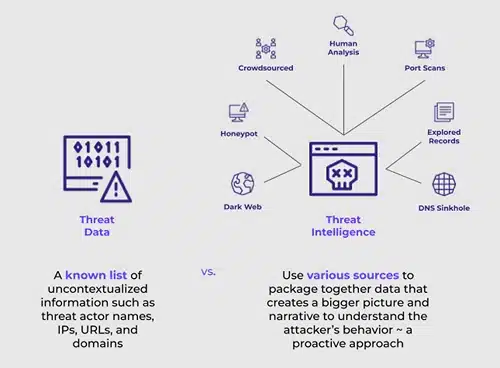
Image Source: security scorecard
Let’s cut through the buzzwords. Threat intelligence is simply knowledge — collected, refined, and actionable — about threats targeting your digital environment. It tells you who might come after you, what methods they are likely to use, and where you are most vulnerable.
But why does it matter? Because in cybersecurity, ignorance is expensive. According to a 2024 Ponemon Institute study, organizations without mature threat intelligence programs took 197 days on average to detect a breach. Those with strong intelligence capabilities shaved that down to just 85 days.
Cyber threat intelligence transforms security from a blind defense into an informed, strategic operation. Instead of hoping your firewalls hold, you actively predict, prepare, and preempt.
In simple terms: you fight smarter, not harder.
How Threat Intelligence Data Is Collected and Made Useful
Picture an intelligence analyst. They are not sitting in a dark room reading secret emails. Instead, they are swimming in a sea of data: suspicious IP addresses, malware signatures, chatter from shady forums, breach reports, and security logs.
Sources can be public, like open-source threat feeds. They can be commercial, like specialized databases. Or they can be internal, such as logs from your firewalls, endpoint sensors, and network monitoring tools.
But raw data alone is not enough. Without analysis, it is just noise.
Good cyber threat intelligence goes through a transformation. Analysts and machine-learning algorithms sift through millions of data points, connecting dots that no single human could process alone. They filter out the false positives, enrich the useful data with context, and deliver something that can actually drive decisions.
For instance, a global retailer might detect a sudden rise in phishing domains mimicking their brand. Threat intelligence teams can pick this up early, allowing legal action and technical blocks before customers are duped.
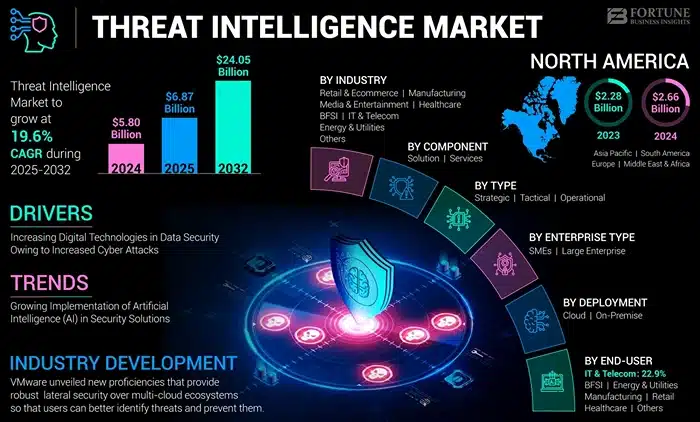
Image Source: fortune business insights
Different Types of Threat Intelligence and Why Each Matters
To really grasp the value of threat intelligence, you need to understand its different flavors. Think of them as layers of armor, each offering protection in a different way.

Image Source: dnsstuff
Strategic Threat Intelligence: The 30,000-Foot View
Strategic intelligence is broad. It looks at big trends — geopolitical tensions, emerging cybercriminal groups, new vulnerabilities affecting entire industries. Business leaders use this to make smart, long-term decisions.
Imagine an agricultural technology company expanding into Eastern Europe. Strategic threat intelligence might reveal increased hacktivist activity in the region, pushing leadership to invest more in local cybersecurity resources early on.
Tactical Threat Intelligence: Knowing the Enemy’s Moves
If strategic intelligence is about why attacks happen, tactical intelligence is about how. It maps out the tactics, techniques, and procedures (TTPs) attackers are currently using.
A financial institution, for example, might learn that a known hacker group is exploiting a flaw in popular mobile banking apps. This knowledge can lead to targeted code reviews and faster patching.
Operational Threat Intelligence: Real-Time, Real-World
Operational intelligence zooms in even closer. It gives detailed information about specific attack campaigns targeting your sector, region, or organization.
Think of an energy provider during a geopolitical crisis. Operational threat intelligence can tip them off that their industrial control systems are being probed, even before any official alerts are issued.
Technical Threat Intelligence: The Quick Hits
This is the most immediate, technical data — IP addresses to block, malware hashes to detect, URLs to avoid. Technical intelligence feeds into firewalls, endpoint protection tools, and monitoring systems automatically.
For instance, a healthcare provider can instantly update their network defenses when technical intelligence reports a new ransomware strain targeting hospitals.
Each layer matters. Together, they create a comprehensive shield, tuned to your organization’s needs.
Threat Intelligence in Action: Real-World Impact
Let’s go beyond theory. In practice, cyber threat intelligence changes the game in several key ways.
Preventing Cyber Attacks Before They Start
A major logistics company, heavily reliant on GPS tracking, used threat intelligence to spot a rise in GPS spoofing attacks across its shipping lanes. They modified routing protocols and trained their crews before attackers could disrupt their supply chains. What could have been a multi-million-dollar crisis was reduced to a non-event.
Sharpening Incident Response
Time is blood during a cyber attack. An insurance firm, recently targeted by a phishing campaign, leaned on operational threat intelligence to understand the specific malware family involved. Instead of fumbling around for days, their security team had actionable steps within hours — isolate affected machines, block known command-and-control servers, and notify impacted clients.
Staying Ahead of a Rapidly Evolving Threat Landscape
Cybercriminals evolve fast. The same retail chain that dealt with phishing attacks later faced a rise in credential stuffing attacks. Thanks to continuous threat intelligence, they adapted their defenses — adding multi-factor authentication, tightening access policies, and shifting user behavior with better education.
Without a steady stream of relevant threat intelligence data, they would have stayed locked in yesterday’s battles, unprepared for today’s threats.
Why Threat Intelligence Must Be Tailored to Your Business
There is no one-size-fits-all solution in threat intelligence. A cybersecurity program that works for a global bank would be overkill — and likely unaffordable — for a regional manufacturing firm. Tailoring intelligence to your specific business needs is not just smart; it is necessary.
Every organization operates in a unique threat landscape. A healthcare provider must worry about ransomware groups targeting patient records, while an e-commerce platform faces constant credential stuffing and payment fraud attacks. Even companies in the same industry can have wildly different risk profiles based on their size, digital footprint, customer base, and regulatory obligations.
The mistake many businesses make is subscribing to broad threat feeds without filtering or contextualizing the data. They end up drowning in alerts that have little relevance to their actual risks.
The best cyber threat intelligence programs start by asking simple but powerful questions:
- Who would want to attack us?
- What would they go after?
- How would they try to breach our defenses?
Answering these questions helps organizations focus on the right intelligence sources, build targeted defenses, and act faster when real threats emerge. In cybersecurity, precision matters — and customized threat intelligence provides that precision.
Challenges and Common Pitfalls in Threat Intelligence Programs
While threat intelligence is a powerful tool, implementing it effectively is not without challenges. Too often, companies invest in intelligence feeds and tools but fail to see a real improvement in their security posture. Understanding the common pitfalls can help organizations avoid costly mistakes.
One major challenge is information overload. Threat feeds can produce thousands of indicators daily. Without a clear filtering process or skilled analysts to make sense of it all, security teams can quickly become overwhelmed. Worse, they may miss the truly important warnings buried in the noise.
Another frequent pitfall is lack of integration. Threat intelligence should not sit in a separate dashboard, disconnected from the broader security operations. If the SOC team cannot easily act on new intelligence — adjusting firewall rules, updating incident response plans, warning vulnerable business units — the value of that intelligence shrinks dramatically.
There is also the risk of relying too much on automation. While automated threat intelligence platforms are incredibly useful, they cannot replace human judgment. Attackers are creative and constantly evolving. Human analysts bring the critical thinking needed to spot nuanced threats and anticipate new attack strategies.
Finally, many organizations forget to measure effectiveness. A good cyber threat intelligence program should answer questions like: Are we detecting threats faster? Are we reducing successful attacks? Are we prioritizing vulnerabilities better? Without metrics, it is impossible to know if intelligence efforts are paying off.
In short, threat intelligence is a living, breathing part of cybersecurity. It demands attention, strategy, and continuous refinement — but when done right, it is one of the most powerful shields a business can build.
Best Practices for Building a Strong Threat Intelligence Program

Image Source: Cyble
Threat intelligence only works if woven tightly into your security fabric. Here’s how smart organizations make it work.
First, know what you need. Not every organization needs nation-state-level intelligence. Tailor your intelligence program to your real risks — your industry, your assets, your threat profile.
Second, integrate it into operations. Intelligence should not sit in a report folder. It should flow into SOC playbooks, security awareness training, patch management priorities, and executive decision-making.
Third, collaborate and share. Join trusted threat intelligence sharing groups in your industry. Shared knowledge often exposes new threats faster than any single company could discover on its own.
Finally, measure success. Are you detecting incidents faster? Responding smarter? Reducing successful attacks? Threat intelligence is not a trophy. It’s a tool, and tools need results.
The Future of Threat Intelligence: Smarter, Faster, Deeper
Looking ahead, threat intelligence will only become more vital. AI and machine learning are already making it faster to detect emerging threats. Big data platforms are allowing deeper, cross-sector insights.
But technology alone will not solve the problem. The human element — skilled analysts, creative defenders, strategic thinkers — will continue to separate great security programs from average ones.
In five years, companies that treat cyber threat intelligence as a dynamic, living part of their cybersecurity strategy will not just survive. They will thrive, outpacing competitors who still operate in reactive mode.
Why Threat Intelligence Is the Competitive Edge You Cannot Ignore
Cybersecurity is not just about defense anymore. It is about intelligence, speed, and strategy. Threat intelligence arms businesses with the foresight they need to stay safe, agile, and ahead.
At PromptCloud, we believe smart data fuels smart defense. Our custom data extraction services help power next-generation threat intelligence strategies, turning overwhelming data into sharp, actionable insights.If your organization is ready to shift from reacting to predicting, from surviving to thriving, let’s talk!